- Topic1/3
23k Popularity
38k Popularity
3k Popularity
301 Popularity
374 Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is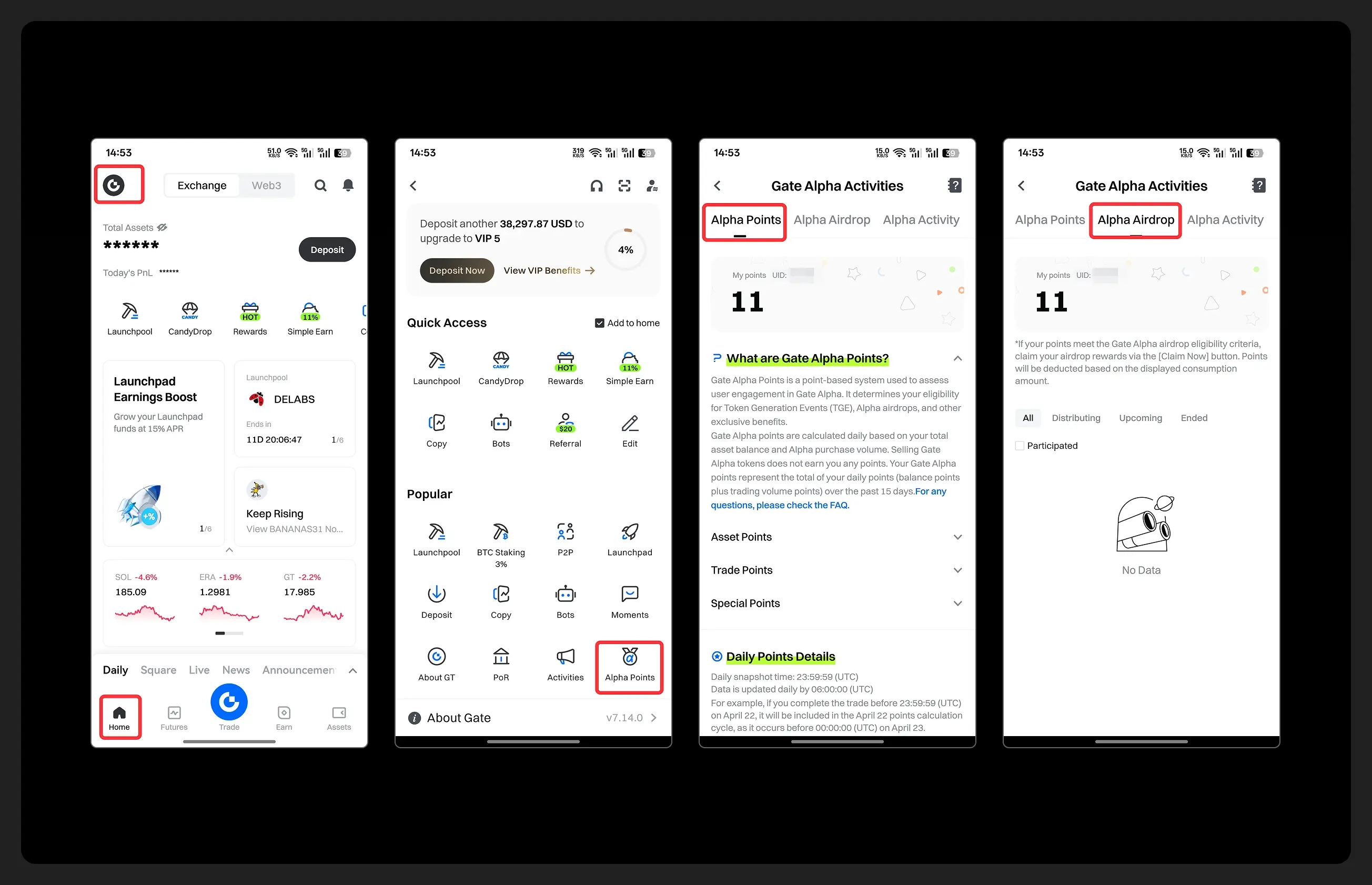
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
North Korean Cryptocurrency Hackers Are Outwitting the World
This article briefly:
· North Korea is reportedly expanding its cyber espionage operation, deploying IT personnel around the world to fund its military ambitions.
· This covert regime specifically targets cryptocurrencies, with an estimated $630 million to $1 billion stolen in 2022 alone.
The increase in North Korean cyber activity underscores the urgent need for greater vigilance and strong cybersecurity measures.
As North Korean cryptocurrency hackers get smarter and more ruthless, they continue to send tremors through cyberspace. According to recent reports, their nefarious activities are rising, morphing and evolving with alarming speed and complexity.
North Korea's secrecy regime is taking advantage of its expanding army of information technology (IT) experts. Its chilling audacity to sidestep international sanctions aimed at financing its military ambitions has put governments around the world on high alert.
The Rise of North Korean Crypto Hackers
U.S. and South Korean officials have recently expressed serious concern about North Korea's plans to send more IT personnel overseas. It is seen as a strategy to boost crypto hacking and bolster military funding.
North Korea is preparing to expand its covert digital workforce in anticipation of an easing of strict COVID-19 lockdowns, according to Jung Pak, deputy special representative of the Democratic People's Republic of Korea.
“It’s a growth industry because we see that North Korea may open up their borders, they may send more labor around the world to generate income. We think it’s getting worse,” Pak said.
Number of cryptocurrency hackers worldwide. Source: Statista
For North Korea, which faces Western sanctions and the severe impact of the COVID-19 pandemic, the cryptocurrency market is a new area of opportunity. The fascination with cryptocurrencies and the rise of information technology has driven countries to increasingly focus on making money from cyberspace.
A shocking UN panel report estimates that North Korean hackers have stolen between $630 million and more than $1 billion worth of cryptocurrencies in 2022 alone. The report highlights that the regime's profit-driven hacking operations are "low-risk, high-reward and difficult to detect, and its increasingly sophisticated practices may hinder attribution."
Battle Tactics: Inside Cyberespionage
North Korean cryptocurrency hackers specialize in identity spoofing. They often conceal their residence, nationality and identity. Moreover, they operate behind fake personas, fake documents and proxy accounts to secure employment across the globe.
They target rich countries and target specific industries such as business, health and fitness, social networking, sports, entertainment and lifestyle.
Kimsuky is a major player in this unscrupulous effort. In fact, the North Korea-based cyber-espionage group is known for stealing weapons and technology for satellite development.
The world's fastest hacker. Source: Statista
This notorious group employs scams, theft, cryptojacking, and sextortion tactics to fund its operations. Furthermore, it cleverly uses cryptocurrencies to conceal its illicit transactions.
Last year, a North Korean company masquerading as a recruiter lured an unsuspecting engineer from blockchain gaming firm Sky Mavis. This malicious Trojan led to the theft of over $600 million — mostly from digital pet game Axie Players of Infinity.
The crypto theft, the country's largest in five years, has poured resources into North Korea's ballistic missile program.
The Global Impact of North Korean Digital Crime
The rampant cybercrime activities of North Korean digital bandits have caused great panic internationally.
Anne Neuberger, U.S. President Joe Biden's deputy national security adviser for cyber and emerging technologies, pointed to a notable spike in large-scale cyber heists targeting encrypted infrastructure. This trend has forced the United States to step up efforts to counter this threat.
Neuberger said, “The real surge last year was targeting centralized crypto infrastructures around the world that hold a lot of money, like Sky Mavis, leading to larger heists. That’s what pushed us to focus on fighting this kind of activity.”
Economic losses caused by cybercrime worldwide. Source: Statista
Interestingly, North Korea’s wave of successful missile launches in recent years has coincided with an increase in cryptocurrency heists. A clear correlation cannot be established due to the opacity of North Korea's financial resources. Still, it's clear that crypto hackers played a major role in funding its missile program.
North Korea has also built a global shadow workforce of IT workers, many from allies such as Russia and China. In fact, these people earn a decent income every year. They are often linked to the regime's cybercrime operations, further compounding the challenge for international investigators.
STRENGTHEN INTERNATIONAL RESPONSE
Given these circumstances, North Korea’s growing cryptocurrency hacking capabilities have drawn global attention. Certainly, their advanced, sophisticated tactics highlight the urgent need for greater vigilance, improved cyber defenses, and greater international cooperation.
As North Korean cryptocurrency hackers get smarter, the world must stay ahead. So keep beefing up your defenses in this high-stakes game of digital cat and mouse.
Global Cyber Security Market. Source: Statista
The disturbing story of North Korea's expanding digital crimes underscores the complex challenges governments, financial institutions and technology companies face today. For this reason, a swift, robust, and coordinated international response is critical to ending these escalating encryption hacks.